DROWN Attack — More than 11 Million OpenSSL HTTPS Websites at Risk
Posted: Mon Mar 07, 2016 5:10 pm
Hacker News




DROWN stands for "Decrypting RSA with Obsolete and Weakened eNcryption."
DROWN is a cross-protocol attack that uses weaknesses in the SSLv2 implementation against transport layer security (TLS), and that can "decrypt passively collected TLS sessions from up-to-date clients."
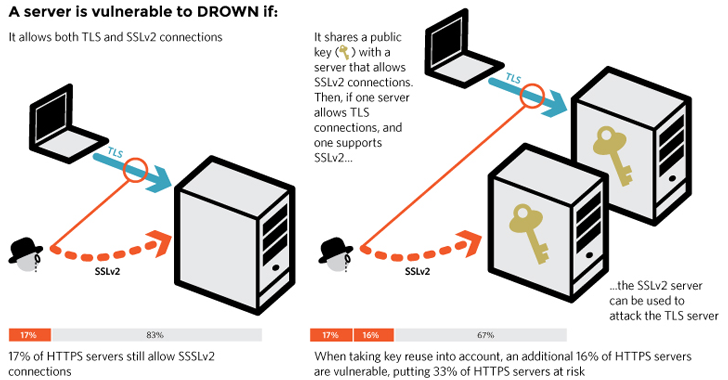
While latest versions don't allow SSLv2 connections by default, administrators sometimes, unintentionally override those settings in an attempt to optimize applications.
"You’re just as much at risk if your site’s certificate or key is used anywhere else on a server that does support SSLv2," security researchers noted. "Common examples include SMTP, IMAP, and POP mail servers, and secondary HTTPS servers used for specific web applications."
DROWN attack could allow an attacker to decrypt HTTPS connections by sending specially crafted malicious packets to a server or if the certificate is shared on another server, potentially performing a successful Man-in-the-Middle (MitM) attack.